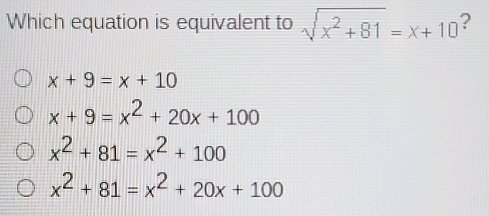
You wouldn’t believe how often confidential information gets compromised—it’s alarming. The Confidential Information Response Monitoring Office plays a crucial role in protecting sensitive data. By implementing proactive strategies and responsive measures, it sets a standard for data security. You’re probably wondering how this office operates and what you can do if you suspect a breach. Understanding these aspects can significantly impact your organization’s integrity and trust.
The Importance of Monitoring Confidential Information
As organizations increasingly rely on digital platforms, monitoring confidential information becomes essential to safeguarding sensitive data.
You must prioritize data security to protect against breaches and unauthorized access. By implementing robust monitoring practices, you enhance information integrity, ensuring that your organization maintains trust and compliance.
Vigilant oversight isn’t just a necessity; it’s a commitment to preserving the freedom and security of your stakeholders.
How the Confidential Information Response Monitoring Office Operates
To effectively safeguard confidential information, the Confidential Information Response Monitoring Office employs a structured approach that combines proactive surveillance and reactive measures.
You’ll find that their confidential analysis identifies potential vulnerabilities, while response strategies swiftly address any breaches.
This dynamic operation ensures a robust defense against threats, allowing you to maintain trust and security in your sensitive information, ultimately fostering a culture of freedom and responsibility.
Key Features of the Hotline Services
While navigating the complexities of confidential information, the Hotline Services offer critical features designed to enhance your security measures.
You’ll appreciate the hotline accessibility, ensuring you can reach support anytime.
Additionally, the service efficiency guarantees swift responses to your concerns, minimizing potential risks.
These features empower you to maintain control over your sensitive data, fostering a safer environment for your operations.
Steps to Take When Reporting a Data Breach
When dealing with a data breach, taking immediate and organized steps is vital to mitigate damage and protect sensitive information.
First, follow your reporting procedures to notify relevant parties. Assess the breach consequences and document everything.
Communicate transparently with affected individuals and regulatory bodies.
Finally, review and strengthen your security measures to prevent future incidents.
Act quickly to safeguard your data.
Conclusion
In today’s digital domain, diligent data defense is crucial. By actively engaging with the Confidential Information Response Monitoring Office, you can contribute to a culture of caution and care. Swiftly reporting suspicious activities through hotline services strengthens security and safeguards sensitive information. Remember, your proactive participation plays a pivotal role in preserving privacy and preventing potential pitfalls. Embrace the responsibility and help ensure a safer, smarter environment for everyone involved.